Singly Linked List
July 8, 2017A Linked List is a fundamental data structure that allows us to easily add new items at any point in the list. Like an array, a linked list is so fundamental that it’s often used internally to hold state for other large data structures. For example, a hash table can be implemented using a linked list internally to store its’ entries.
All various forms of a linked list make use of nodes, which we can simply define as:
public class LinkNode<TElement>
{
public TElement Element { get; set;}
public LinkNode<TElement> Next { get; set; }
}
Nodes for all the various forms of a linked list share the Element property. What differs is the pointers, such as Next. The simplest of linked lists, the Singly Linked List, keeps a single pointer per node that points to the next node in the list.
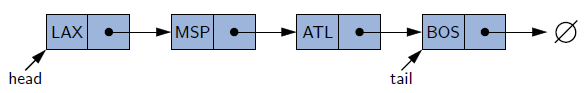
At the minimum, a reference to the head of the linked list must be kept since a linked list is composed of reference type objects. It’s recommended to keep a reference to the tail as well such that we can easily add a new item to the very end of the list. Without a reference to the tail, we would need to traverse the entire list just to add it.